Relying on the industrial alliance, China's many agricultural machinery technology has been a breakthrough
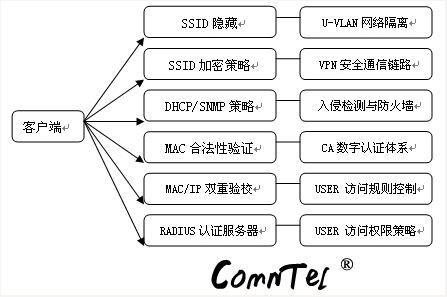
1, hidden SSID number SSID (hidden service set identifier) ​​can generally be obtained through the terminal scan, wireless bridge supports hidden service set identifier (SSID), that is, the device does not broadcast SSID, so the wireless terminal can not automatically scan to obtain the SSID, the terminal must Proactively provide the correct SSID number to associate with the wireless bridge. Therefore, we only need to hide the SSID number and there is no way to scan the SSID number we use. There is no way to directly establish a connection with our wireless bridge.
2. WEP (Wired Equivalent Privacy Mechanism). The wireless network implements the encryption mechanism based on the shared key in the 802.11 protocol. It is called the "Wired Equivalent Privacy" technology. WEP is an RC-4 based algorithm. 40bit or 128bit encryption technology. The mobile terminal and the wireless router can be configured with 4 sets of WEP keys, which can be used in turn for encrypting and transmitting data, allowing the encryption keys to change dynamically. High encryption level, basically meet the needs of ordinary business users.
To ensure the security of data transmission, a group of devices that communicate with each other, the encryption algorithm, and the encrypted content must be the same, otherwise communication cannot be performed normally. This is our most common form of encryption.
3. MAC address filtering MAC (physical address filtering control) uses a hardware control mechanism to implement the identification of accessing wireless terminals. Because the network card of the wireless terminal has a unique MAC address, if the MAC address filtering mechanism is enabled, the bridge cannot be allowed to communicate with the terminal only when the MAC address of the client is valid. In other words, the devices that communicate with each other can bind their MAC addresses to each other. The device only allows the devices that exist in the MAC address list to communicate with each other.
Specifically how to achieve the wireless bridge encryption, please call Shenzhen Laien technology and technical personnel, we have professional and technical personnel for your guidance.
1) Plastic Squeezing Granulator is our new designed machine, made by the advanced Italian techniques, specially screw pressing design;
2) This machine is used in recycling machine industry, especially for plastic film, plastic bags, woven bags, jumbo bags, solve the drying problem in the past;
3) Instead of the dewatering machine, hot blower in the recycling line and energy saving equipment;
4)Suits for PP/PE film and PP woven bags;
5)Highly improve quality and productivity of the PP/PE granulating line;
6)Moisture of the final pellets: <2%
7) Easy to operate
Plastic Squeezing Granulator,squeezing dryer granulator,film squeezing pelletizing machine,plastic film squeezer pelletizer
zhangjiagang sevenstars machinery co.,ltd , https://www.sevenstars-machineries.com